Netgear UTM10B-10000S Datasheet Page 2
- Page / 4
- Table of contents
- BOOKMARKS
Rated. / 5. Based on customer reviews


Simple Setup, Ease of Management
The ProSecure UTM will easily replace any existing firewall or router. A simple 10-step setup
wizard guides you through installation and the UTM will be up and running in minutes.
Administration is performed through an intuitive Web-based interface. Set granular policies
and alerts, check summary statistics and graphical reports, drill down to IP address-level data,
and integrate log data with standard network management tools using SNMP. Malware and
IPS signature, software, and firmware updates are all handled by the UTM - online
and automatically.
For many administrators and IT personnel one of their biggest nightmares is the management
of individual licenses or “seats.” Buying additional licenses when computers and personnel are
added to the network is time-consuming and costly. The ProSecure UTM offers Web and email
protection subscriptions with no “per-user” licensing.
ProSecure
®
Unified Threat Management Appliance UTM Series
• SSL & IPsec VPN
Remote Access
– SSL VPN - clientless remote access,
anywhere, anytime
– IPsec VPN - secure site-to-site tunnels
and client-based remote access
– No additional licenses to purchase
• Built-in SPI Firewall
– Dual/Quad WAN Gigabit Firewall**
provides load balancing and failover
– Gigabit LAN ports, configurable
hardware DMZ port
– Stateful packet inspection (SPI)
– Denial-of-service (DoS) protection
– IPS prevents hackers from penetrating
the network perimeter
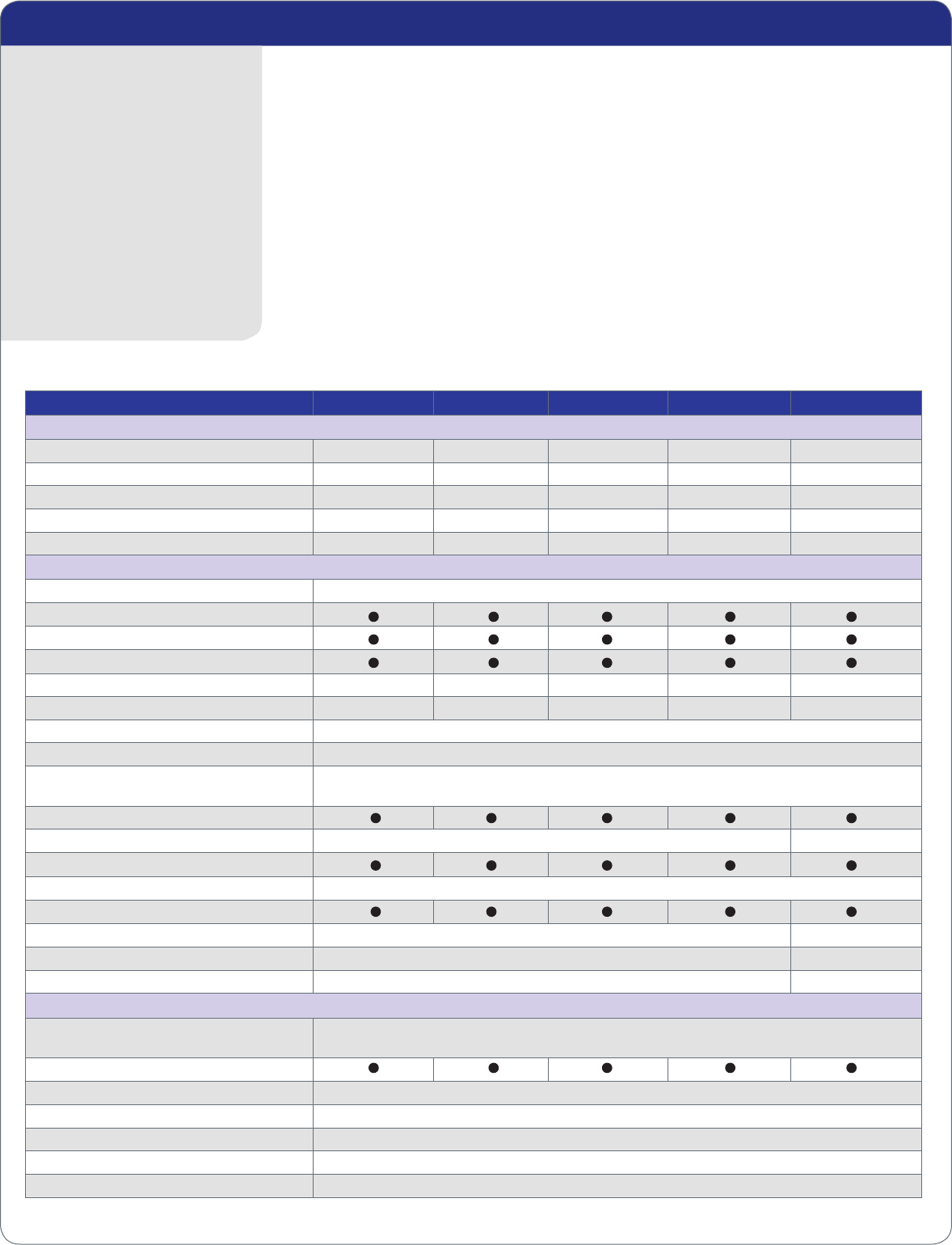
UTM SERIES COMPARISON
MODEL UTM5 UTM10 UTM25 UTM50 UTM150
SIZING GUIDELINES
Average Anti-virus Throughput¹ 15 Mbps 20 Mbps 25 Mbps 45 Mbps 130 Mbps
Stateful Packet Inspection Firewall Throughput¹ 90 Mbps 90 Mbps 127 Mbps 400 Mbps 900 Mbps
Maximum VPN Throughput¹ 40 Mbps 50 Mbps 70 Mbps 200 Mbps 400 Mbps
Maximum Concurrent Connections¹ 8,000 12,000 27,000 40,000 65,000
VLANs 255 255 255 255 255
CONTENT SECURITY
Web and Email Scanned Protocols HTTP, HTTPS, FTP, SMTP, IMAP, POP3
Stream Scanning
Inbound and Outbound Inspection
Signature-Less Zero Hour Protection
Malware Signatures 1.2 Million 1.2 Million 1.2 Million 1.2 Million 1.2 Million
Automatic Signature Updates Hourly Hourly Hourly Hourly Hourly
Web Content Filters Filter By: HTML Body Keywords, File Extension
Web Object Filters ActiveX, Java™, Flash, JavaScript™, Proxy, Cookies
Email Content Filters
Filter By: Subject Keywords, Password-protected Attachments,
File Extension, File Name
Distributed Spam Analysis
Distributed Spam Analysis Supported Protocols SMTP, POP3
Anti-spam Real-time Blacklist (RBL)
User-defined Spam Allowed/Block Lists Filter By: Sender Email Address, Domain, IP Address, Recipient Email Address, Domain
Distributed Web Analysis w/64 categories
Instant Messaging (IM) Control MSN
®
Messenger, Yahoo!
®
Messenger, mIRC, Google Talk
Peer to Peer (P2P) Control BitTorrent™, eDonkey, Gnutella
Maximum Number of Users Unlimited
FIREWALL FEATURES
Stateful Packet Inspection (SPI) Port/Service Blocking, Denial-of-service (DoS) Prevention, Stealth Mode, Block TCP Flood,
Block UDP Flood, WAN/LAN Ping Response Control
Intrusion Detection & Prevention (IPS)
WAN Modes NAT, Classical Routing
ISP Address Assignment DHCP, Static IP Assignment, PPPoE, PPTP
NAT Modes 1-1 NAT, PAT
Routing Static, Dynamic, RIPv1, RIPv2
VoIP SIP ALG
 (2 pages)
(2 pages)







Comments to this Manuals